A common threshold range criteria must be established for vulnerability scores related to the vulnerability object. When assessments are run, vulnerability scores are derived according to the threshold range. Before running an assessment, ensure that the threshold range is configured to meet your assessment's auditing guidelines and policies.
Each configuration range allows the user to adjust the threshold range by specifying the numeric value, unique name, color, and the option to display text or a score.
In order to adjust the configurations, you must have the Tenant Configure permission.
To set up Vulnerability Risk Configuration:
Open the Threat and Vulnerability Manager.
- Go to Configuration > Vulnerability Risk Configuration.
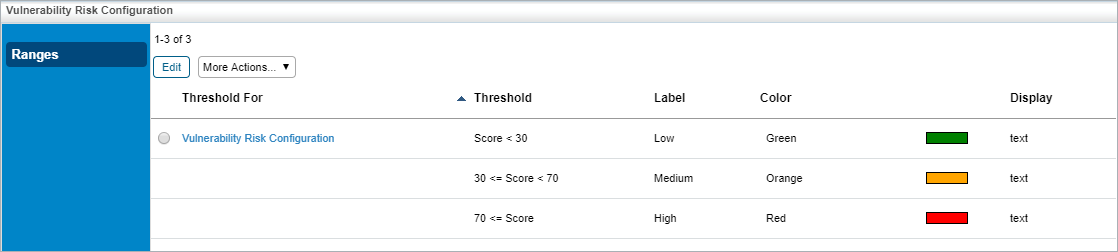 The Vulnerability Risk Configuration tab.
The Vulnerability Risk Configuration tab.
- Select Vulnerability Risk Configuration and click Edit.
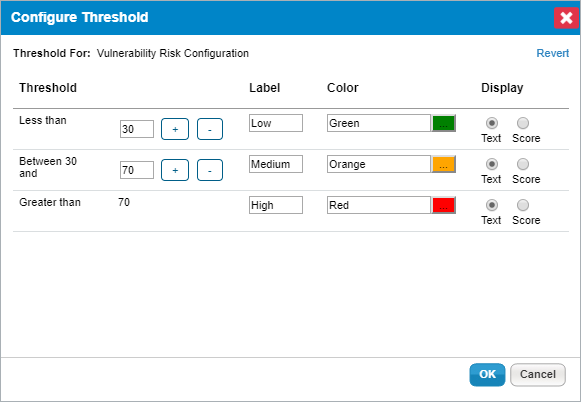 The Configure Threshold dialog.
The Configure Threshold dialog.
- Click + or – to add or remove a threshold range. For any assessment configuration, you can add a maximum of five threshold ranges. At a minimum, any configuration range contains two threshold ranges.
- Optional:
To modify a range, enter a numerical value in the threshold range field.
- To change the threshold display name, enter a name in the label field.
- To assign a color for a threshold, click the Color icon, choose the desired color, and click Close.
- Choose the Text or Score option to display the threshold label or the value for the risk after the assessment is run.
- Click Revert to ignore all changes or click OK to save.




